Horus 53 was the first launch in the Project Horus Member Payload launch program, which features new payloads developed by AREG club members. This launch’s payload was the brainchild of Derek VK5TCP, and was a Hak5 ‘WiFi Pineapple’, a wireless penetration testing device which was configured to log all WiFi access points it observed, but also broadcast a WiFi access point for observers to try and connect to. Also flying was the usual array of telemetry beacons, and a Wenet imagery payload.
Launch preparations went smoothly, and with excellent (if maybe a little cold) weather, Horus 53 was launched just after 10AM on the 25th of August 2019, by the youngest member of the launch crew – Tom:
With launch complete, the balloon filling gear was quickly packed up and the chase teams departed. Chasing the balloon this flight was:
- Team QI: Mark VK5QI, Will VK5AHV and Chris VK5FR
- Team Derek: Derek VK5TCP and Derek VK5RX
- Team LJG: Liam VK5LJG (Solo)
- Team WTF: Marcus VK5WTF + IMD product
While Mark, Derek and Liam’s teams were focused on recovering the payloads, Marcus’s aim was to situate himself directly under the balloon flight path and try and connect to the flying WiFi access point (more on this later!).
The chase on this flight was fairly uneventful – the balloon ascended as planned, and burst at an altitude of 31.659km. The chase teams headed out along the Karoonda highway, and were able to get well ahead of the balloon and wait near the predicted landing site.
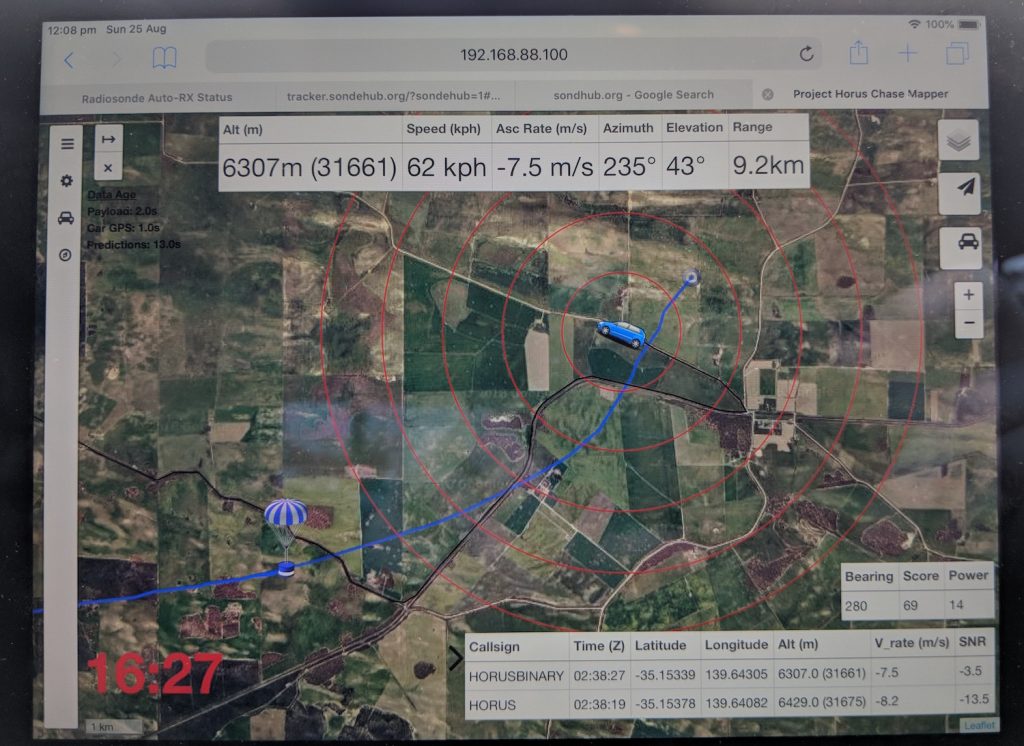
View of the chase-car mapping software near the end of the flight, as is used by the chase teams to navigate.
All throughout the flight the Wenet payload was downlinking stunning imagery of the state:
With the permission of the landowner, the chase teams were able to access the property where the payloads were predicted to land, and positioned themselves to try and watch the landing. Unfortunately the wind model was incorrectly predicting the ground-level winds as being higher than they really were, and the payloads dropped almost straight down for the last 500m or so, to land right in a tree right next to the road the chase teams had just been on 5 minutes earlier! The Wenet payload was hanging nicely in a tree, and was able to capture images of the chase teams arriving on-site just a few minutes after landing.
All the payloads (and quite a bit of the balloon…) were accounted for and in good condition, though the wind-vane that adorned Derek’s WiFi Pineapple payload was nowhere to be seen, and likely tore off at balloon burst.
WiFi Pineapple Payload Results
Derek’s payload performed perfectly throughout the flight, though the narrow beam-width of the antenna used on it did mean it only saw a few tens of WiFi access points. mainly near the beginning and end of the flight. The WiFi access point was connected to successfully during the flight by Marcus VK5WTF, who recounts his experience below:
Equipment at my end was a Linux laptop running Kismet software, with a USB WiFi adaptor (AWUS036H) plugged into a 2.4 GHz gridpack I picked up a Gippstech two years ago. As a backup I also took my own WiFi Pineapple Nano, just to send out SSID beacons for the payload to pick up.
Looking at the predicted path I marked a few places I could use as ground stations, mostly around the Karoonda Hwy. The plan was to set up a table and lay the gridpack on its back pointing straight up, and I found the perfect sized plastic tub to do the job.
First location was the Sunnyside Lookout north of Murray Bridge. Here I could test scanning for the payload and have a first attempt at connecting to it.
At this location I was also getting a lot of other WiFi Access Points that would have been de-sensing the receiver, and the poor front to back of the gridpack antenna would have also been an issue.
After roughly 15 minutes I got my first glimpse of the payload in Kismet as it was going through the 13 km mark somewhere above my head. When I saw VK5ARG come up on my screen, I definitely got excited, the theoretical is reality. But the two minutes I spent checking everything, I lost valuable time before attempting a connection. It was at the peak of its pass when I started (10:54 ACST), and my log shows I made several associations but near immediate drop out, like it was getting about a 0.5-2Hz spin, “:20 trying to associate”, “:20 associated”, “:21 disconnected” occurred 24 times in the log over roughly 70 seconds.
Off to site two, and the current prediction had it going over the site of the old Kulde train station, so that’s where I headed. Once set up, I found that I had enough phone reception to see where the balloon was, but I didn’t need it, Kismet was seeing the SSID already, time to attempt a connection. Height was about 7km, and it was flying about 4 km by ground west north west of me.
In and connected first try (12:09 ACST), but not getting a lot of data, then the connection dropped, likely still spinning, lets try again… Bam, I’m in! From here the connection stayed up and was strong until it started raining and I disconnected everything; but I was connected for around 3 minutes. At the time I disconnected the height was 4.6 km, and by ground the payload was around 3km north east. Remember that my antenna was pointed straight up in the opposite direction of gravity.
What was I doing with that couple of minutes? Solving the encrypted messages left on the homepage of the Pineapple.
The first was “SGFtIFJhZGlvIGlzIGdyZWF0Lg==”. Easy peasy, base64, answer: “Ham Radio is great.”
The second was a little more difficult, mainly because there wasn’t a command line linux application to do the job for me. The cipher text: “Cjmpn ovfzn Cvh Mvydj dioj ocz nft rdoc Kdizvkkgzn.” Immediately this looked like a rotation (Caesar) cipher maybe ROT13, so I started writing something in Python; and then the rain came, so cancel that! When I got home, I put a little more work into the second cipher, and the characters where shifted by 5, to reveal the answer “Horus takes Ham Radio into the sky with Pineapples.”
Great job Marcus! Derek is currently working on an upgraded version of this payload with a newer WiFi Pineapple model and better antennas, so it’s likely we’ll be trying this again in the future.
Telemetry Statistics
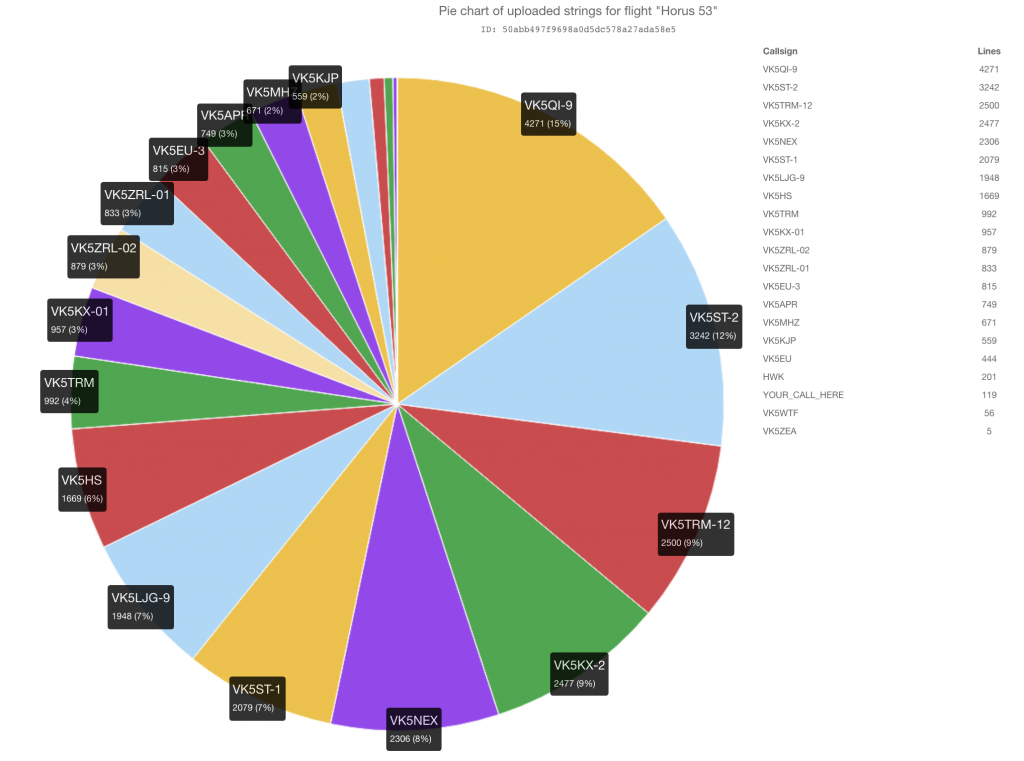
Once again, we had a great showing of amateur radio operators from around the state receiving telemetry form the balloon, including a few new callsigns decoding the Wenet imagery.
The statistics from the various payloads flown are shown in the tables below:
RTTY Payload
| Callsign | Received Packets | Percentage of Flight Received | First-Received Altitude (m) | Last-Received Altitude (m) |
|---|---|---|---|---|
| VK5APR | 736 | 62.5% | 1583 | 4746 |
| VK5EU | 438 | 37.2% | 12549 | 1829 |
| VK5EU-3 | 797 | 67.7% | 7777 | 2173 |
| VK5KX-01 | 944 | 80.1% | 1772 | 4598 |
| VK5MHZ | 658 | 55.9% | 1425 | 6152 |
| VK5QI-9 | 840 | 71.3% | 353 | 24 |
| VK5ST-2 | 836 | 71.0% | 3694 | 2173 |
| VK5TRM | 977 | 82.9% | 2984 | 2780 |
| VK5ZEA | 5 | 0.4% | 9953 | 9063 |
| VK5ZRL-01 | 824 | 69.9% | 2704 | 5354 |
| VK5ZRL-02 | 865 | 73.4% | 2461 | 6214 |
4FSK (Horus Binary) Payload
| Callsign | Received Packets | Percentage of Flight Received | First-Received Altitude (m) | Last-Received Altitude (m) |
|---|---|---|---|---|
| HWK | 233 | 11.8% | 18980 | 4215 |
| VK5HS | 1156 | 58.9% | 10500 | 2323 |
| VK5KJP | 415 | 21.2% | 6735 | 2147 |
| VK5KX-2 | 1738 | 88.6% | 1166 | 4157 |
| VK5LJG-9 | 1228 | 62.6% | 1877 | 65 |
| VK5NEX | 1610 | 82.1% | 2880 | 4558 |
| VK5QI-9 | 1533 | 78.2% | 351 | 65 |
| VK5ST-1 | 1444 | 73.6% | 3290 | 1512 |
| VK5ST-2 | 1687 | 86.0% | 3061 | 1911 |
| VK5TRM-12 | 1743 | 88.9% | 1814 | 1413 |
| VK5WTF | 40 | 2.0% | 12631 | 13389 |
Wenet Imagery Payload
| Callsign | Packets Received | Total Data Received (MiB) |
|---|---|---|
| VK5APR | 206546 | 50.43 |
| VK5DSP | 23917 | 5.84 |
| VK5EU | 6561 | 1.60 |
| VK5EU-2 | 29187 | 7.13 |
| VK5FISH | 151574 | 37.01 |
| VK5QI (Mobile) | 118730 | 28.99 |
| VK5KX | 133667 | 32.63 |
Thanks to all who participated in receiving the telemetry from this flight – all uploads are much appreciated, and help make the flight much more enjoyable for those spectating from home.
Conclusion
Thanks again to all involved with preparation, launch, tracking and chasing. With an influx of interest in this aspect of the amateur radio hobby, we’re hoping to ramp up the frequency of Project Horus launches, but to do this we need your payload ideas to launch! If you have a payload you would like to fly, take a look at the Project Horus Member Payload Launch Program page and let us know your ideas!
Catch you all at the next flight! 73 VK5QI
Horus 53 - Flight Statistics
| Metric | Result |
|---|---|
| Flight Designation: | Horus 53 |
| Launch Date: | 2019-08-25 00:35:51Z |
| Landing Date: | 2019-08-25 02:53:17Z |
| Flight Duration: | 2 Hours 18 Minutes |
| Launch Site: | -35.07668,138.85643 |
| Landing Site: | -35.12053,139.70958 |
| Distance Traveled: | 78 km |
| Maximum Altitude: | 31,645 m |